Home » PROFESSIONAL SERVICES AND TRAINING
Professional Services &
Training
Professional Services
Get the best performance and results out of our products and solutions with certified training, implementation, configuration and other product related services.
We regularly hold training and technical workshops as well as offering on-site assistance with deployment, configuration, upgrades and other services. Ask us how we can help you optimise your investment in cybersecurity solutions.
As companies have responded to Covid-19, they have had to rapidly transform their workplaces with new technology, infrastructure and policies that accommodate a distributed/remote workforce. At the same time, malicious online activity has increased as scammers try to take advantage of consumers and businesses in this new environment. To support ESET customers during this challenging time, ESET has introduced Health Check to help companies of all sizes strengthen their IT security policies and infrastructure.
Since the service’s April 2020 soft launch, over 100 companies have taken advantage of the custom Health Check service, in which a dedicated ESET engineer conducts a comprehensive assessment that includes discovery, inspection, ESMC (ESET Security Management Center) authentication and verification, best practices, and advice on next steps. Health Check is being offered direct to customers and through ESET channel partners who have access to Health Check “campaign in a box” training and marketing support.
Our engineers will look at the following and make
appropriate recommendations on what they find:
- Review alerts, alarms, and detections
- Review management server health
and performance - Review product licensing and versions
- Review endpoint health
- Review policies
- Review notifications
- Review invalid objects
We are more than happy to provide you with a Proof of Concept and cost estimates. Please click the link below to get in touch with us.
Vulnerability management solutions are only valuable when they help you prioritize your efforts effectively. Tripwire® IP360™ is an enterprise-class vulnerability management solution that enables cost-effective reduction of cyberthreat risk by focusing your remediation efforts on the highest risks and most critical assets.
HOLISTIC VISIBILITY
INTEGRATED VM ECOSYSTEM
FLEXIBLE & SCALABLE
ACTIONABLE REPORTING
Whether you’re a security analyst, administrator or CISO, Tripwire Connect has vulnerability reports and analytics that address your needs.
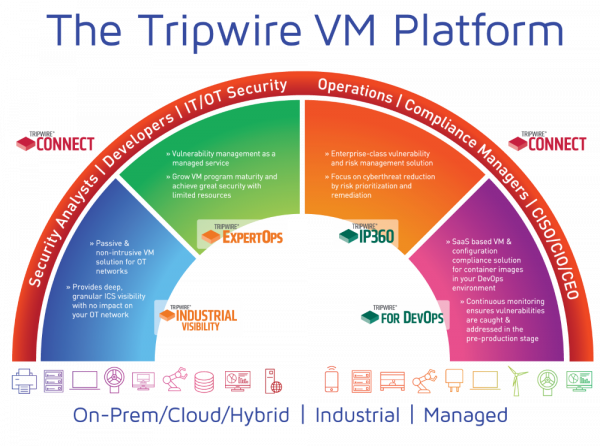
 Tripwire IP360 gives you complete network visibility both on-premises and in the cloud. The Tripwire Vulnerability and Exposure Research Team (VERT) keeps Tripwire IP360 up to date with accurate, non-intrusive discovery signatures. Our unique application-centric approach to vulnerability scanning and assessment searches for specific vulnerabilities based on operating systems, applications and services. This ensures only the required signatures are run, limiting negative application interactions. Rather than providing a seemingly endless list of “high risk” vulnerabilities, Tripwire IP360 does risk scoring on limitless, time-based scale, making it clear where your risk lies so you can focus on the most effective mitigations first.
Tripwire IP360 gives you complete network visibility both on-premises and in the cloud. The Tripwire Vulnerability and Exposure Research Team (VERT) keeps Tripwire IP360 up to date with accurate, non-intrusive discovery signatures. Our unique application-centric approach to vulnerability scanning and assessment searches for specific vulnerabilities based on operating systems, applications and services. This ensures only the required signatures are run, limiting negative application interactions. Rather than providing a seemingly endless list of “high risk” vulnerabilities, Tripwire IP360 does risk scoring on limitless, time-based scale, making it clear where your risk lies so you can focus on the most effective mitigations first.
Click here to download the Tripwire IP360 Datasheet
 Tripwire Connect is a highly-customizable analytics, reporting, integration and management platform for Tripwire Enterprise and Tripwire IP360 that deploys and scales according to your organization’s needs. Dashboards provide clear, actionable insights so you can address the most urgent concerns first. Incremental transmission for all data from Tripwire Enterprise enables real-time reporting, and the ability to aggregate deltas of change data reduces network bandwidth and speeds analysis. In addition, high-demand data fields bolster compliance and file integrity reports. Tripwire Connect is available either on-prem or as a SaaS. Tripwire Connect provides instant insights into your security posture thanks to integrated data from multiple security tools displayed at once.
Tripwire Connect is a highly-customizable analytics, reporting, integration and management platform for Tripwire Enterprise and Tripwire IP360 that deploys and scales according to your organization’s needs. Dashboards provide clear, actionable insights so you can address the most urgent concerns first. Incremental transmission for all data from Tripwire Enterprise enables real-time reporting, and the ability to aggregate deltas of change data reduces network bandwidth and speeds analysis. In addition, high-demand data fields bolster compliance and file integrity reports. Tripwire Connect is available either on-prem or as a SaaS. Tripwire Connect provides instant insights into your security posture thanks to integrated data from multiple security tools displayed at once.
Click here to download the Tripewire Connect Datasheet
We provide a range of security awareness training courses for businesses and end-user alike.
We are currently running security awareness training for Cofense email phishing protection. For more information about this course, please click the link below.
Cofense Cybersecurity Awareness Training for Employees
Please contact us for further info on this course
ESET PROTECT Training courses:

For EDR we have 2 different courses:
- Certified ESET Enterprise Inspector Deployment Specialist
- Certified ESET Enterprise Inspector Optimization Specialist
The deployment course goes over alarm management, rules and exclusion creation. (highlighted below)
We currently don’t run these as an instructor led. But we do have people sitting these courses.
About this Learning Plan (Certified ESET Enterprise Inspector Optimization Specialist)
This Learning plan is aimed at technical staff like security analysts, administrators, network specialists etc., who deal with security issues of organizations on a technical level. The training will give them an insight in using ESET Enterprise Inspector with the primary focus on optimizing the environment. It will also demonstrate the potential to find suspicious or malicious activity by analyzing alarms and work with rules and exclusions. The learning plan represents one of the technical certification modules, which is required from “Enterprise” focused resellers, based on the ESET Global Partner Program.
Course Expenses:
Please note that this 2-day course is $500 NZD in total for both days. After registering for the course, you will be sent an invoice for the course expense. Once payment is received, you will be accepted into your course of choice.
Prerequisites:
- Advanced knowledge of operating system (MS Windows)
- Basic knowledge of TCP/IP networking
- Basic knowledge of computer networks
- Basic programming and scripting
Proficiency level:
Expert
After completion:
After completing the learning plan, students will be able to:
- Understand the principles of multi-layered protection, recognize the purpose of individual protection layers and have an overview of the technologies used in ESET solutions
- Identify ESET home and business products
- Understand ESET PROTECT architecture and role of individual EP components. They will be able to install the EP Server, deploy EM Agents to client computers in the network, subsequently manage their EP environment and work with the EP Web Console (groups, tasks, policies, reports and access rights) on a basic level
- Install ESMC Server, deploy EM Agents and ESET security products globally in large networked environments, set up product activation and updates in offline environment, install EEI Server and deploy EEI Agents in various ways, install EEI Server and deploy EEI Agents in various ways
- Navigate through EEI Web Console and find the required information, optimize EEI according to the given environment, find suspicious or malicious activities by analyzing alarms (detections) and understand as well as create Rules and Exclusions.
Certification:
Certified ESET Enterprise Inspector Optimization Specialist
Products covered:
- ESET Endpoint Security for Windows
- ESET PROTECT
- ESET Full Disk Encryption
- ESET Server Security for Windows
- ESET Remote Deployment Tool
- ESET Enterprise Inspector
- ESET LiveGrid
- ESET Endpoint Security
- ESET Security Management Center

LogRhythm Platform Administrator (LRPA) Certification
301 – Administration Fundamentals
301 – Administration Fundamentals is a 16-hour instructor-led training, providing attendees with hands-on learning and best practices for the basic day-to-day administration activities performed within the LogRhythm Platform.
Module topics include:
- An Introduction to LogRhythm with a Platform Overview
- Log Source Administration
- Install and Configure System Monitor Agents to Collect Log Sources
- Alarming and Reporting
- Health Monitoring and Maintenance
- Tuning and Restoration
302 – Advanced Intelligence (AI) Engine Fundamentals
302 – Advanced Intelligence (AI) Engine Fundamentals is an 8-hour instructor-led training, providing attendees with hands-on learning and best practices for AI Engine Rule development and functionality through the LogRhythm SIEM.
Module topics include:
- An Introduction to AI Engine and AI Engine Rules
- Observed, Threshold, and Unique Values Rule Blocks
- Behavioral Rule Blocks
- AI Engine Tuning
Who should attend 302 and 301 courses?
301 – Administration Fundamentals is designed for systems administrators, engineers, and other LogRhythm users who are responsible for the basic maintenance and configuration of the LogRhythm Platform.
302 – AI Engine Fundamentals is designed for systems administrators, engineers, SIEM Administrators, SIEM content creators, and other LogRhythm users who are responsible for the maintenance and configuration of the LogRhythm Platform.
Prerequisites:
We recommend participants have Windows and Linux experience as well as command-line experience.
Some additional recommendations include (but are not limited to):
- Introduction to LogRhythm – What is a SIEM
- Introduction to LogRhythm – Administrators and Analysts
- What’s New in LogRhythm v7.5
- Web Console – An Introduction Video
305 – Analyst Product Training
The 305 – Analyst Product Training is a three-day In-person Instructor Led, Virtual Instructor Led, or Onsite Instructor Led training course that targets the basic day-to-day analytical activities performed within the
LogRhythm Platform.
Who Should Attend
305 – Analyst Product Training is designed for security analysts, systems administrators, engineers, and other
LogRhythm users who are responsible for the day-to-day analysis of the data in the LogRhythm Platform.
Prerequisites:
Participants are required to complete the following computer-based training (CBT) modules prior to arrival at
305 – Analyst Product Training:
• Introduction to LogRhythm: What is a SIEM?
• Introduction to LogRhythm: Administrators and Analysts
Participants must pass a ten-question quiz at the end of each course, with a score of 70% or more, to receive
credit for completion.
305 – Analyst Product Training
305 – Analyst Product Training explores the day-to-day activities in the LogRhythm Platform for analysts.
Participants are introduced to the features and tasks that enable analysts to optimally perform Threat Lifecycle
Management (TLM).
The course includes hands-on exercises to provide experience with the analytical functions of the LogRhythm
Platform. Participants can expect to leave with an understanding of analytical functions within the LogRhythm
platform and will be equipped with the tools to effectively analyze the log data collected.
This training consists of the following modules:
• Day One: Analyst Fundamentals
• Day Two: Security Analytics
• Day Three: AI Engine Fundamentals
305 – Analyst Product Training
Day One: Analyst Fundamentals
Reducing the time to detect and respond to threats largely determines an organization’s ability to avoid damaging cyber incidents. The Analyst Training course introduces the steps taken during Threat Lifecycle
Management (TLM) to reduce the mean-time-to-detect (MTTD) and mean-time-to-respond (MTTR) to threats.
This training consists of the following modules:
• The Role of an Analyst
• Navigating the Web Console
• The Analyst’s Tasks
• Customizing the Web Console
• Challenge: Taking Action as an Analyst
Day Two: Security Analytics
Security analysts develop practical hands-on application of the features and functionality of the LogRhythm
tools needed to perform Threat Lifecycle Management. This training consists of the following modules:
• Security 101
• Security Types
• Threat Lifecycle Management in the SIEM
• Practice Exercise: Ransomware Attack
• Challenge: Botnet Detection
• Challenge: Reducing Downtime
• Challenge: Comply with Acceptable Use Policies
Day Three: AI Engine Fundamentals
AI Engine Training explores the administrative activities for the AI Engine. Participants can expect to leave
with an understanding of how AI Engine functions, an understanding the configuration of AI Engine Rules, and
common threats and attack scenarios for which the rules are configured to monitor. The course is comprised
of the following topics:
• Introduction to AI Engine
• AI Engine Rules
• Threshold and Unique Values Rule Blocks
• Behavioral Rule Blocks
o Whitelist
o Statistical
o Trend
Certification
LogRhythm Security Analyst (LRSA)
By attending and completing the training, participants will be prepared to take an exam to obtain the
LogRhythm Security Analyst (LRSA) certificate.
The LRSA exam is a written exam comprised of multiple-choice questions testing a candidate’s knowledge on
using the LogRhythm platform for the analysis of data. Candidates will have 90-minutes to complete the
exam. Candidates must pass the written exam with a score of 70% or more to receive a LogRhythm Security
Analyst (LRSA) certificate. If a passing score is not obtained, candidates must wait 30 days before taking the
exam again.
Whether you’re starting to build a SOC or you need to mature an existing one, Chillisoft’s implementation services can help you align the technology of your SIEM with the process and people of your SOC, improving both analyst efficiency and leadership visibility. Our Implementation consultants can help you understand and assess your organization’s security operations maturity and areas for improvement. You’ll also learn how to define timelines and staffing requirements to ensure success. Specifically, our team can help you:
• Build an adaptive architecture
• Automate and accelerate your responses (SOAR) capabilities
• Hunt and investigate threats
• Use advanced analytics to detect threats across the
holistic attack surface
• Integrate threat intelligence
Looking to upgrade your Business Secruity with ESET? Look no further than ESET NZ Cloud Managed service – Complete outsourcing, monitoring and management of your ESET Security Service. Click the link below to contact us about what software you are wanting to upgrade.

The ability to connect your business systems to customers and suppliers via the cloud, browsers and smartphones has created huge opportunities. However, it has also brought unprecedented security risks – malware, phishing, ransomware and more. We specialise in protecting companies from cyber attacks. It’s all we do, every day, all over the world.
Black Box Penetration Testing
In a Black Box test, we have no knowledge of any of your internal information structures and are not given access to your applications or network. This test is the most similar to a real-world malicious attack and usually requires significant time (as we need to attempt many attack methods to ensure none of them works), and deeper vulnerabilities may not be found or exploited during the time frame of the test.
However, simply because deeper vulnerabilities cannot be found doesn’t mean they don’t exist, which can result in a false sense of security that could be exploited at a later date by a hacker without time constraints waiting for the right opportunity.
White Box Penetration Testing
In White Box testing, we have complete access to your selected networks, systems and applications, which allows us high-level privileges and the ability to view source code. We perform both dynamic and static analyses to identify weaknesses across several areas such as security misconfigurations, logic vulnerabilities, poorly written software code and more.
This type of penetration test is comprehensive as both internal and external vulnerabilities are identified, assessed and prioritised from a ‘behind closed doors’ perspective that is not available to most hackers.
Grey Box Penetration Testing
In a Grey Box test, our team replicates the activities that a hacker would undertake after they have penetrated your security perimeter and has internal access to your network. You provide us with some background information such as network infrastructure maps, application flow charts and low-level credentials, which allows for much more streamlined and efficient testing, saving time and money.
This approach also allows us to focus on identifying and exploiting potential vulnerabilities in your higher-risk systems rather than attempting to discover where these systems are.
