Network Detection and Response
Network Detection and Response (NDR) is a burgeoning field of cybersecurity that enables organizations to monitor network traffic for malicious actors and suspicious behavior, and react and respond to the detection of cyber threats to the network. The rise of NDR systems reflects the growing number of systemwide attacks by criminal actors ranging from hackers to nation-states.
Read about our NDR solutions below …
 ESET Grey Cortex.
ESET Grey Cortex.
Network Traffic Analysis.
Network traffic analysis tool exploiting artificial intelligence, machine learning and big data to ensure secure IT operations for enterprise, government and critical infrastructure users.
- Round-the-clock security monitoring
- Powerful rapid detection & response capabilities
- Deep visibility into the internal network
- Easy to use functionality
Identify Threats Before Damage Happens
Many other providers focus on known methods of attack or pieces of malicious code. Using advanced artificial intelligence methods, MENDEL
goes beyond known threats to detect and identify symptoms of malicious behavior at the atomic level. Threats are identified in their early stages,
decreasing incident response time, preventing further damage, and reducing overall risk. MENDEL also adds integrated signature-based detection and known threat intelligence; increasing its detection capabilities, while reducing the
false-positive rate.
Automatic Adaptation
MENDEL’s unique Network Behavior Analysis engine (NBA) uses advanced mathematical analysis in machine learning to generate and adapt
detection rules from past traffic. It integrates inputs from its other detection engines and includes specialized algorithms which, among other
functions, distinguish between machine and human behavior. MENDEL’s NBA engine is the only solution on the market which offers this ability.
MENDEL’s Advanced Security Network Metrics protocol allows it to monitor over 70 features of each individual network flow. This advanced level of analysis makes MENDEL more effective at detecting malicious behaviour and other threats than solutions on the market today.
More Sensitive Detection
MENDEL’s advanced data mining techniques ensure that it can process many more data flow features than solutions based on NetFlow protocols, in real time. Furthermore, MENDEL can scale up to 10Gbps in a single sensor and collector configuration, and up to 40Gbps per collector.
View more info on ESET’s website.

Extrahop – Reveal(x) Network Detection and Response for a Secure Enterprise.
Cloud adoption, tool sprawl, and increasingly advanced encryption are challenging resource-strapped security teams to rise above the noise of legacy tools and workflows so they can protect and accelerate their hybrid enterprise.
ExtraHop Reveal(x) is the industry leader in network detection and response (NDR), providing complete east-west visibility, real-time threat detection inside the perimeter, and intelligent response at scale.
Automated Inventory
Reveal(x) ensures an always up-to-date device inventory with no manual effort by auto-discovering and classifying everything that talks on the network.
Peer Group Detections
By automatically sorting devices into highly specific behavioral peer groups, Reveal(x) can spot strange behavior with minimal false positives.
Perfect Forward Secrecy Decryption
Reveal(x) decrypts SSL and TLS 1.3 encryption passively in real time so you can maintain visibility while leveraging the latest encryption standards.
Advanced Machine Learning
With machine learning using 5,000+ features, Reveal(x) detects, prioritizes, and surfaces threats against your critical assets.
Automated Investigation
Reveal(x) contextualizes detections from an entire transaction with threat intelligence, risk scores, and asset criticality for easier triage and response.
Confident Response Orchestration
Reveal(x) handles detection and investigation while powerful integrations with solutions like CrowdStrike, Phantom, Demisto, and Palo Alto Networks help you automate remediation.
See more info …
Get the RevealX data sheet here
Netskope Private Access (NPA) is a cloud-based Zero Trust Network Access (ZTNA) solution that is a fully integrated component of the wider Netskope Security Cloud platform and delivered through the global Netskope NewEdge network. NPA directly connects remote workers to private applications running in public cloud environments or private data centers; reducing risk and simplifying security operations. NPA allows an organization to begin retiring legacy VPN hardware, and move towards a more secure, cloud-first, remote access architecture. End the high capital investment, refresh cycles, and ongoing management costs of VPN appliances —and adopt ZTNA for your remote access need
Zero Trust Network Access for private applications
Provide authorized users with access to their applications – not the whole network – and protect private applications and other network assets from malicious insiders or compromised accounts.
Connect directly to public cloud applications
Connect remote workers directly to applications hosted in public cloud and private data centers using Netskope’s globally hosted network of PoPs. This provides an architecturally elegant and low-latency end user experience for accessing private applications.
Phase out legacy VPN remote access
Retire legacy VPN hardware and enable a move towards a cloud-first security architecture. Phase out the capital investment, refresh cycles, and ongoing management costs of VPN appliances.
Protect private applications and resources
Ensure that private applications hosted in public and private cloud are never exposed to the Internet. Avoid brand damage, fines, and remediation costs associated with a breach of a private application hosted in the cloud.
Seamless and transparent user experience
Use a unified, lightweight client, to provide users with simultaneous access to all of their applications deployed across public cloud and data centers without the hassle of connecting and reconnecting to various VPN gateways.
Begin your transformation to a SASE
Use a single administrative console for simplified policy management, analytics and incident investigation for employee use of web, cloud and private applications. Move towards the cloud-based future of network security – Secure Access Service Edge (SASE).
View the Netskope NPA Datasheet here

Firewall-as-a-Service (FWaaS) enables consolidation, less complexity, and lower cost of operations
Netskope Cloud Firewall (CFW) provides network security on outbound traffic across all ports and protocols for users and offices. CFW policy controls include 5-tuple (source and destination addresses and ports with protocol), plus user-IDs and group-IDs, fully qualified domains and wildcards as destinations, an application layer gateway for FTP, and tracking events for firewall logging.
Unrivaled visibility. Real-time data and threat protection.
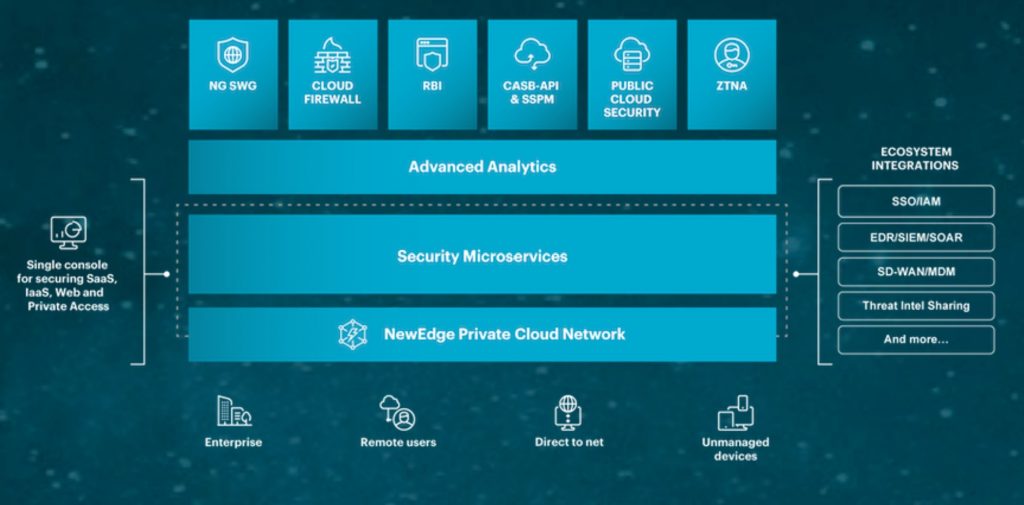
The Netskope Security Cloud provides unrivalled visibility and real-time data and threat protection when accessing cloud services, websites, and private apps from anywhere, on any device. Only Netskope understands the cloud and takes a data-centric approach that empowers security teams with the right balance of protection and speed they need to secure their digital transformation journey.
Features and benefits

Firewall policy controls
Include 5-tuple (source / destination address and port, protocol), user-IDs and group-IDs, FQDNs and wildcards for egress firewall policy settings.

FTP application layer gateway
Enables seamless use of FTP through cloud edge network address translation services.

Firewall event logging
Full logging of all desired CFW events (TCP, UDP, ICMP), available for export or as part of Netskope Advanced Analytics.
Integrated SASE architecture
CFW, SWG, CASB, ZTNA, RBI and Advanced Analytics with one platform, one console, one policy engine, and one client to enable consolidation and less complexity.

Cloud scale and performance
NewEdge provides cloud scale and performance and removes the issues of firewall appliances, hair pinning traffic, and a poor user experience.

Lower cost of operations
Reduce appliance expenses and maintenance, dependency on endpoint firewalls, and administration efforts with multiple consoles.
